By Apolo Kakaire |
The Internet which is viewed as the panacea for democracy, participation and inclusion is increasingly becoming a tool of repression deployed by regimes across the world to stifle rights and voice. Africa, a continent already replete with poor democratic credentials and practices seems to be rapidly catching up on the new ‘epidemic’- digital authoritarianism.
The use of technology tactics to advance repressive political interests has come to be referred to as digital authoritarianism. However, the tactics employed by authoritarian regimes have also been deployed by democratic states for purposes of surveillance, spread of misinformation, disinformation, and the disruption of civic and political participation under the pretext of fighting cybercrime, and in the interest of protecting national security, and maintaining public order.
Big technology companies are key drivers of digital authoritarianism through the creation, innovation and supply of repressive technology and related support. Moreover, political parties, interest groups, and smaller private companies have lapped it up too, developing and using tools and strategies of digital authoritarianism.
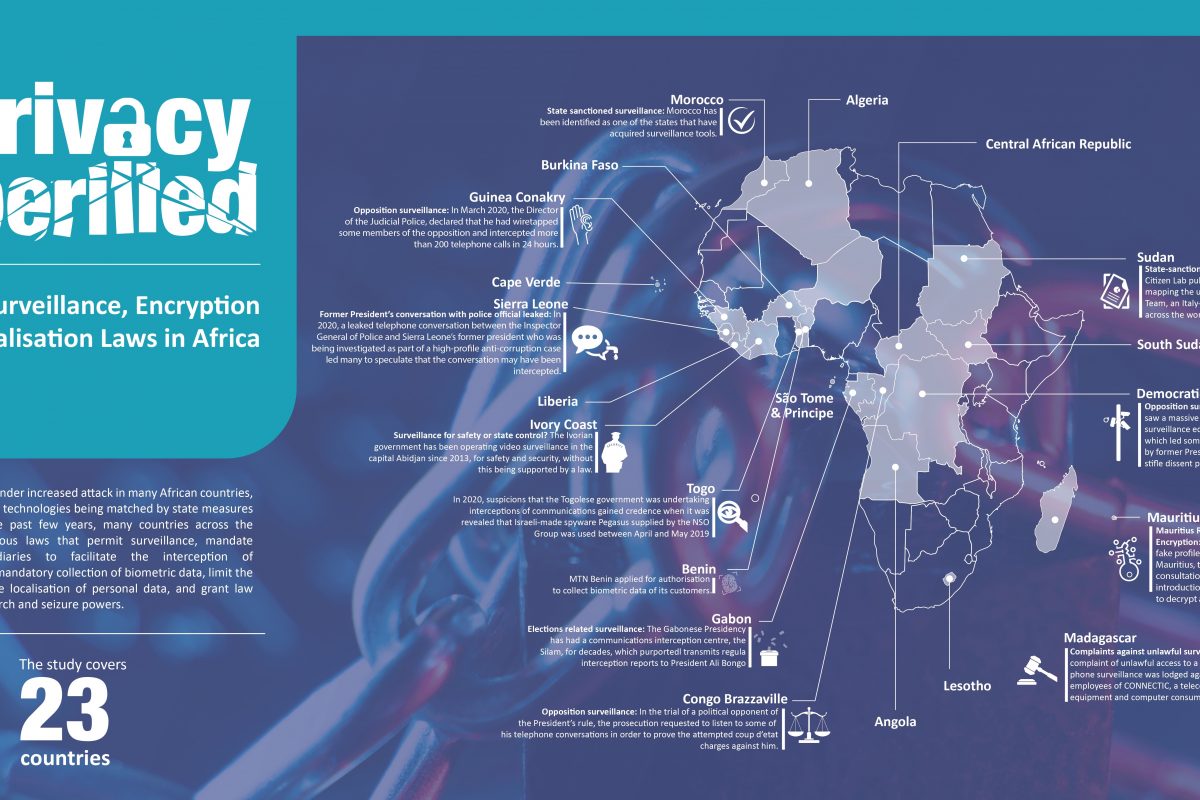
Digital authoritarianism is a great case study in understanding and appreciating the impact of technology on human rights. While laws legalising surveillance and interception of communications, and widespread data collection and processing may not be a problem in themselves, it is the ambiguity often present within those laws that give governments wide latitude of interpretation to facilitate the rights abuse that is a growing challenge.
At the Forum on Internet Freedom in Africa 2022 (FIFAfrica22), Global Voices Advox, shared findings from the Unfreedom Monitor– a project exploring the political and social context that fuels the emergence of digital authoritarianism in 17 countries. They hosted a panel discussion in which project researchers from India, Nigeria, Sudan and Zimbabwe presented the project findings on the connections between political contexts, analogue rights, and the growing use of digital communications technology to advance authoritarian governance.
The findings paint a grim picture for freedom of the media, expression, and democracy in general. In Zimbabwe for instance, the Unfreedom Monitor report notes that; “the press walks a precarious line between national security and the professional obligation to report truthfully” on issues that happen in the country. It is an observation that is replicated in the mapping conducted in Morocco, Egypt, and Tanzania
In Sudan, where internet censorship, bad laws and repressed liberties and network disruptions are commonplace, Khattab Hamad noted that the contours and motives of digital authoritarianism include fear of losing power, protecting the existence of regional or international alliances, and geopolitical motives protecting private and family interests. He added that terrorism and support for terrorist groups was another motive for authoritarianism in the country.
In Tanzania, researchers found that often, laws are enacted as precursors to enable various methods of digital authoritarianism. For example, the Cybercrime Act which was hurriedly enacted just months before the October 2015 elections. “There were many other such laws, including the amendments to the Non-Governmental Orgnaisations (NGO) Act, that saw NGOs being deregistered and control on them tightened in the lead up to the 2020 elections”, they revealed.
In Uganda, network disruptions in the run up to and during recent elections is another example of digital authoritarianism. “Sometimes the internet is restored after elections. So, the question is what exactly is the purpose? What are you hiding? Why do you deny your people access to information? Internet shutdowns also question the credibility of elections”, said Felicia Anthonio of Access Now. She added that network disruptions affect engagement between voters and political candidates, in addition to limiting electoral oversight and monitoring by human rights activists and election observers.
As part of the Unfreedom Monitor project, Global Voices Advox has established a publicly available database on digital authoritarianism to support advocacy in light of the “urgency of a fast deteriorating situation”, said Sindhuri Nandhakumar, a researcher with the project.
While applauding the research and database in supporting evidence-based advocacy, digital rights activists at FIFAfrica22 noted that given the behaviour of authoritarian regimes, advocacy at the national level may be met with a lot of resistance. As such, more engagement was called for through special mandates and periodic human rights review mechanisms at the African Union (AU) and the United Nations Human Rights Council.
“Advocacy [against digital authoritarianism] at national level will be difficult. Positive results could be registered through Special rapporteurs at the AU and states through the Universal Periodic Review (UPR), towards securing accountability”, said Arsene Tungali from the Democratic Republic of Congo.
For African digital rights activists, the Global Voices Advox research and database unravels new avenues for collaborative advocacy and transnational opportunities for interventions to stem this spread of digital authoritarianism. The findings however also point at the need for a concerted and robust response to its growing traction.
As elections in Africa remain a major flashing point for digital authoritarianism as all manner of manipulation of voters, narratives, even results abound, it remains a key area of transnational cooperation. Ahead of the elections in Zimbabwe, slated for July-August 2023, Advox will come up with tips on awareness raising on voter rights and the role of technology in elections. Zimbabwe provides a good opportunity to pilot, learn and perhaps adopt some interventions to counter this behemoth.